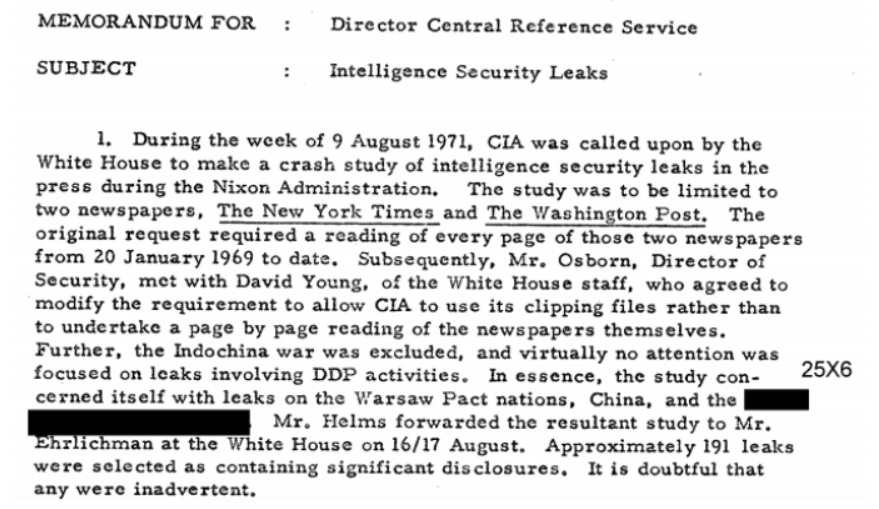
In August of 1971, the White House directed Central Intelligence Agency to conduct a “crash study of intelligence leaks” that had appeared in the press since the beginning of the Nixon Administration on January 20, 1969. The study was quickly completed, and has been requested in a new FOIA, but it resulted in a new proposal - an Agency created and maintained database of past and present leaks to help track their damage and identify the leakers. While ultimately successful, the creation of the database raised some unexpected questions for the Agency, such as who should be responsible for it, what counted as a leak, and did the Agency care?

In a memo dated August 20, 1971, Walter Pforzheimer, the curator for the Historical Intelligence Collection, proposed the creation of a CIA-run database of intelligence leaks in response to the recent White House requested study of intelligence leaks. Providing background, Pforzheimer notes that between January 1969 and August 1971, the Agency identified approximately 191 that constituted “significant disclosures.” Notably, this was only from the New York Times and the Washington Post, and excluded leaks relating to the Indochina war and DDP activities. To Pforzheimer and others, this constituted a serious problem (though as shown in the excerpt above, there was some question about whether or not the concern would persist).
Pforzheimer approached the matter fairly methodically, beginning with the basic question of “what is a leak?” Ignoring the considerations of the Nixon-requested study, Pforzheimer gave the straightforward and fairly inclusive answer of “any unauthorized disclosure of intelligence sources and methods, or disclosure of intelligence estimates, reports, studies, facts or figures which would tend to reveal either intelligence sources or methods or the extent of our information on a given subject.” The more complex question was what was an authorized leak and what was unauthorized? Pforzheimer argued authorized leaks could be just as dangerous as unauthorized ones, potentially more due to the greater access to classified materials. The question of how to respond to authorized and pseudo-authorized leaks would have a major impact on a number of Agency personnel, such as Ray Cline, and their handling of press contacts.

While several Agency components had already kept files on the leaks, Pforzheimer noted that they were largely incomplete. The Office of Security’s (OS) files, for instance, dealt largely with major leak investigations and where the identity of CIA personnel had been publicly exposed in the media. Other components similarly suffered from incomplete and scattered records on the subject of leaks.

Pforzheimer felt that these issues went hand in hand with the Agency’s “absence of a good, centralized database” dealing with intelligence leaks. This had impacted the quality and speed of both the more recent “crash study” and previous studies, such as the 1964 attempt to source Wise and Ross’ Invisible Government and the 1966 damage assessment regarding the New York Times’ publication.

In the following section, Pforzheimer again raises the lack of a centralized data base. Reconstructing information such as severity of leaks or what they correlated to after the fact is often difficult and time consuming. Pforzheimer felt that, going forward, the Agency would need a centralized database to avoid losing “a stunning number of manhours [trying] to work it out” long after the fact.

At the conclusion of his memo, Pforzheimer finally formally proposed the creation of just such a centralized database. Pforzheimer felt that the OS should maintain the file, but that “all elements of the Agency should contribute to it on an all source basis.” Other offices could also perform the function in theory, but would have a harder time getting full cooperation from the various Agency components. The creation of such a file would require “the full backing of the Deputies and the [Director] so that every Office would be responsible for producing an annotated description and damage assessment of leaks.” Without the input and active involvement from every office, the effort would be doomed to fail. As Pforzheimer noted, the breadth of information that needed to be covered meant that no one could assess all of the leaks without help from others.

The proposal was fairly well received throughout the Agency, though there was some disagreement on the proper execution of the project. Howard Osborn, CIA’s Director of Security, argued that it should be under the purview of the Directorate of Intelligence rather than the OS. Osborn felt that the OS’ responsibilities laid with investigating leaks, assigning responsibility and taking “remedial steps if warranted.” Osborn felt that the database would be “an effective tool for use by [intelligence] analysts in their evaluations and reporting of the majority of unauthorized disclosure cases.”

Osborn’s argument produced an odd “Quo Vadis?” (where are you going?) question, with the remainder of the comment redacted for being “illegible.”
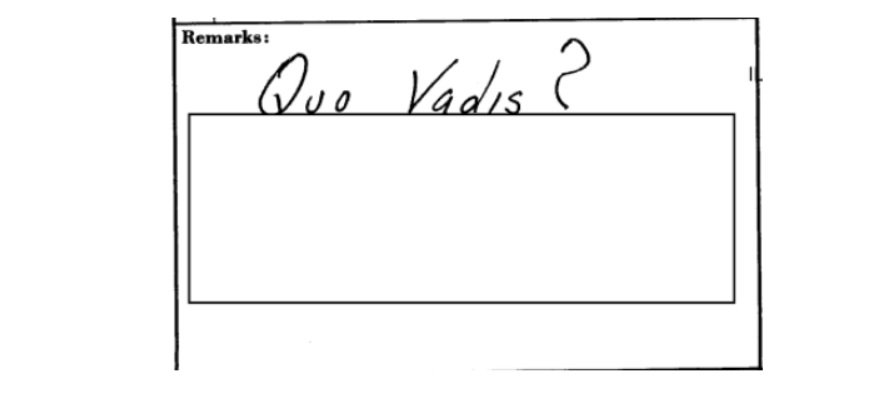
Osborn’s argument was ultimately put aside, and responsibility assigned “formally and irrevocably” to the OS.

By October 4th, Osborn had accepted that it would ultimately be responsible for the project. In his memo, originally classified SECRET, Osborn wrote that the OS was “prepared to establish and maintain a centralized data base covering leaks.” Detailed information on each leak would be submitted to the OS, which would then process and organize it for cross-referencing.

The memo specified that initially the database would analog and manually operated, but that they should switch to a computerized database as the number of leak reports grew.

By the end of the month, Colby signed off on a memo making the policy official. Colby’s memo largely repeated the recommendations in Osborn’s memo, memorializing them in an official format.

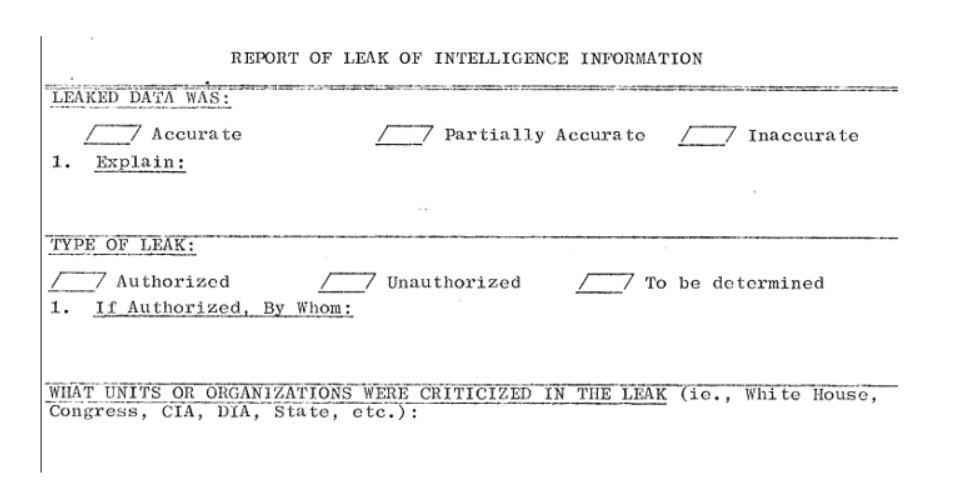
The form for reporting the leaks, based off Osborn’s and Colby’s recommendations, was fairly comprehensive. In addition to any supplemental materials, which were be attached to the leak reports, the form was two pages long. In addition to requesting the time, date, publication author and how the sourcing was attributed, the form requested notes about the subject matter, the geography associated with it and the dissemination of the information. After asking what, if anything, the information had compromised, the form asked about the accuracy of the information.
The form also requested information about whether the leak was authorized or not, and who had authorized it. Tellingly, it requested information about which government organizations were criticized in the leak, but didn’t feel the need to ask who or what had been praised.
In a previously SECRET memo sent shortly after Colby’s memo, a senior Agency officer reported that there was agreement throughout the Agency that the database should begin manually and be expanded when the volume of data required it.
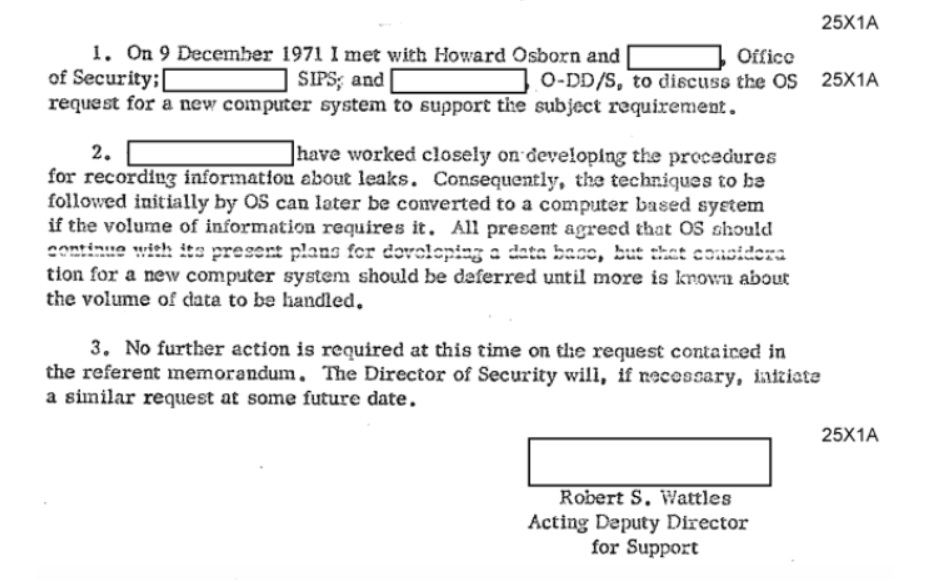
In another SECRET memo, Osborn reported that the needs of the system would likely be unique, and that a new computer system would be required for it. Nevertheless, initial plans were already underway to build the computer system they would need.
The Agency continued with the database program over the next several years, though it would take sometime for the program to be centralized throughout the Intelligence Community.

An undated, previously CONFIDENTIAL, memo written sometime after August 1973 noted that the Agency had identified 312 leaks and entered them into the database.
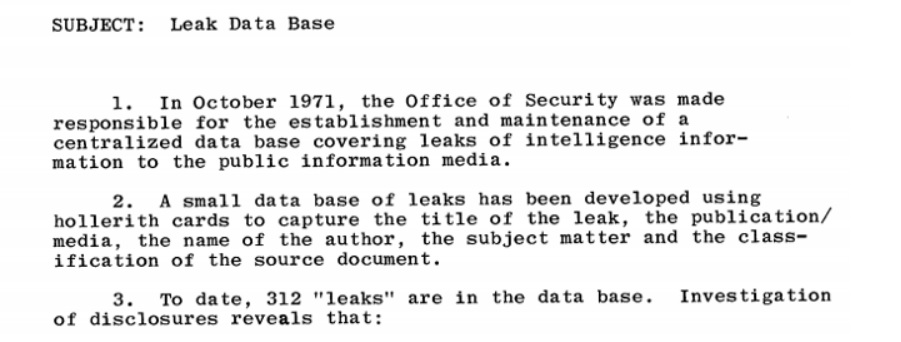
The database had enabled them to quickly answer queries about various leaks in what was described as an effective and inexpensive system. It was not uncommon for the fruits of these efforts to be provided to the White House, where Dr. Kissinger took a special interest in them.

The database’s creation marked a turning point in the Agency’s approach to leaks, and laid some of the groundwork for the leak hunts seen by various Administrations since then. Since it’s creation, the database’s functions have been expanded and streamlined. One can only imagine how such a database reacted to the sheer volume of materials leaked by Chelsea Manning and WikiLeaks, or later Edward Snowden.
The database’s expansion and growth will be explored in a future article. In the meantime, you can read the submission form embedded below.
Like Emma Best’s work? Support her on Patreon.
Image via Wikimedia Commons




