Terrorism analysts have noted how savvy the Islamic State is on social media. The White House and think tanks alike point to Twitter support for ISIS as a key metric for the group’s strength. Similar worries once swirled around MySpace and Second Life as platforms for recruiting homegrown jihadists.
A 2008 report commissioned by the Army envisions how a mastermind halfway around the world might leverage social networks for terrorism. In the fictional case study, a jihadist targets a lonely Detroit teenager via MySpace, connects the boy with a sleeper cell, trains him on Second Life for weeks, and orchestrates a suicide attack that kills dozens of people.
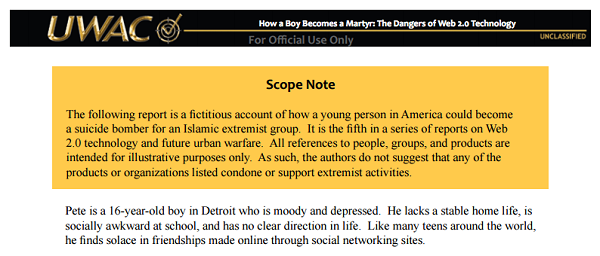
The report,“How a Boy Becomes a Martyr: The Dangers of Web 2.0 Technology”, was posted online in 2010 by the Public Intelligence website. It was compiled by the Urban Warfare Analysis Center, a now-defunct “dedicated center of excellence” sponsored by the U.S. Army Research Laboratory and run by a military contractor.
Notably, the report came out four months after Facebook overtook MySpace as the top social network worldwide.
Its six pages spin a wildly improbable yarn about technology’s appropriation by murderous zealots. The report proposes no solutions or assessment as to its feasibility, but offers only “a fictitious account of how a young person in America could become a suicide bomber for an Islamic extremist group.”
We open on Pete, a 16-year-old in Detroit who is “socially awkward” and in need of a father figure. Jafar, a jihadist living in Lebanon, sends Pete a friend request from his own MySpace account and several fake ones, and introduces the young man to Islam. Unbeknownst to his friends and family, Pete is soon spending hours online socializing with Jafar and a global Muslim community.
The report neglects to note whether Jafar makes Pete’s top 8. We quickly pivot from MySpace to Second Life, where Pete creates an avatar “with dark skin and stylish clothes” to make himself appear Middle Eastern. Jafar steers Pete toward Muslim spaces within Second Life, and encourages his moldable protege to make the Virtual Hajj to the replicated Mecca.
Pete is unaware that Jafar controls many of the avatars he meets inside Second Life. The terrorist mentor stages a conversation on the topic of jihad within earshot of Pete, and soon puts the teenager in touch with a band of radical jihadists living just outside Detroit. Now radicalized himself, Pete resolves to carry out an attack.
“Pete feels like a champion,” the report summarizes of Pete’s excitement at being chosen for jihad. “He finally won at something.”

Jafar settles on the stadium for “the local professional basketball team” as the target. (Note that the report cites MySpace and Second Life by name, but not the Pistons. Even I know the Pistons play in Detroit.)
Second Life facilitates Pete’s training and prep for the attack, from “an exact three-dimensional virtual blueprint” of the arena constructed by rabid fans of “local professional basketball” for training to “a virtual ticket booth” to purchase tickets. Pete rehearses the attack over 200 times on a private virtual island inside the game.
On the fateful day, Jafar leads Pete to a secret location inside Second Life, where he ”is welcomed as a champion by what seems like thousands of Muslims.” Once again, all of these adoring fans are bots controlled by Jafar as part of the plot.
Pete straps up with a martyr vest, sneaks inside the arena according to plan, and takes his seat at midcourt. He stands and detonates just after opening tip off while screaming “Allahu Akbar!”
Other blasts go off simultaneously, each planted by coordinated teams who were also trained inside Second Life without ever having met each other.
“Only Jafar knew the entire plan,” the report emphasizes.
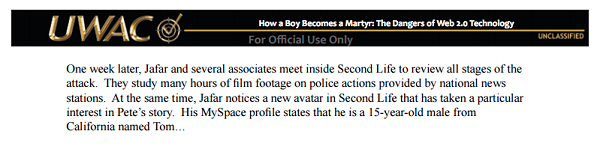
We close on the mastermind erecting a Second Life shrine to Pete and his fellow martyrs, then turning his gaze toward a 15-year-old in California, who of course, just happens to be named Tom.
This is just one of several reports produced by the Urban Warfare Analysis Center on government contract. Other UWAC titles include:
- “Cell Phone Use by Insurgents in Iraq”
- “Threat Analysis: Hamas and Hezbollah Sleeper Cells in the United States”
- “Web 2.0 and Enemy Recruitment”
- “Virtual Worlds and their Implications for Urban Warfare”
- “Virtual Worlds and Terrorist Attack Planning”
MuckRock has requested all UWAC reports, as well as contracts between the UWAC contractor and the Army.
Where policy experts, military officials and community leaders are now tackling Twitter as a terrorist tool and a powerful means of countering extremist ideologies, there is scant evidence that earlier social networks aided jihadists in training.