The New York Police Department says it has no record of cell phone surveillance or interference conducted on protestors at the 2014 Millions March NYC.
Compelled by a recent New York Supreme Court decision in Millions March NYC v. NYPD, NYPD made the claim after more than a year asserting it “can neither confirm nor deny” possession of such materials in response to a 2017 Freedom of Information Law request from the organization Millions March.
Millions March is a Black Lives Matter-affiliated protest group that was involved in a 25,000-person police brutality protest following the murder of Eric Garner by a Staten Island police officer in 2014. During the demonstration, members experienced suspicious issues with their phones, some of which were shutting off at random or receiving messages indicating possible interference with Signal, an encrypted messenger app.
The group, concerned about NYPD surveillance of demonstrators’ cell phones, filed a FOIL request for records on the department’s technology use: cell phone interference at protests, monitoring of protestors’ social media accounts, and surveillance of other groups and organizing activities. In part, they wanted to know if the NYPD had been using equipment known as cell site simulators. Requests on these devices are commonly rejected, often on the basis of “security” or “trade secrets”. NYPD, in this situation, issued what is known as a “Glomar response”: a vague and sweeping denial of a public records request that is usually only deployed when dealing with highly sensitive national security issues.
Represented by the New York Civil Liberties Union, Millions March sued.
The case was stayed last year in anticipation of a final decision from the New York Court of Appeals on Abdur-Rashid v. NYPD, another case that called into question NYPD’s use of the Glomar response, but which was decided in favor of NYPD in March 2018. Despite this, on January 14th, the Millions March case was decided in favor of the plaintiffs, and the court ruled that NYPD’s use of the Glomar was inadmissible when the information isn’t pertinent to an ongoing criminal investigation.
Over the past two years, MuckRock has worked to compile information from local, state, and national law enforcement agencies on their use of cell phone surveillance devices, also known as cell site simulators, IMSI catchers, Stingrays, or Triggerfish. Through public records requests, we’ve uncovered details about these programs such as their cost and device sharing practices, and we have received revealing exemptions or refusals, including a Glomar, from a good number of agencies. But the Glomar response is rare, in part because local and state police departments have a very limited right to use it.
The decision in Millions March NYC v. NYPD is a significant rebuke to law enforcement efforts to expand the use of the Glomar doctrine, NYCLU Media Strategist Naomi Dann said in an email to MuckRock.
“A state court, in a well-reasoned opinion, sharply limited the scope of Glomar denials and explained why vague, attenuated connections to anti-terrorist police work are not sufficient to upend public records laws’ presumption of public disclosure,” she wrote. “This doesn’t bind any other courts or any other states, but courts in other states could find it persuasive.”
What are cell site simulators?
A “StingRay device” disguises itself as a normal cellphone tower, allowing a phone within radius to connect to it. Once connected, law enforcement, depending on the device in use, can gain access to a variety of personal information.
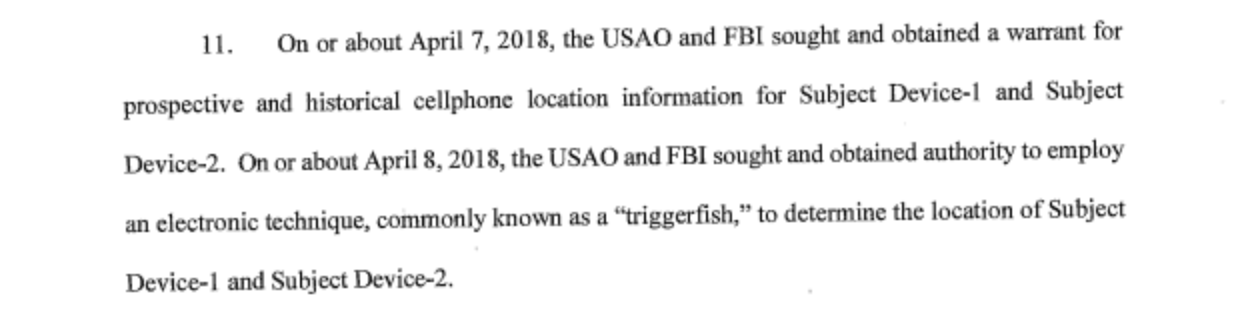
If it’s an IMSI catcher, or a “passive device,” law enforcement can use it to find and log your phone’s unique identifying International Mobile Subscriber Identity (IMSI) number, which they can use to track you. If it is a cell site simulator, or an “active device,” then once your phone connects to it law enforcement could theoretically conduct a sweeping data search of your phone and any accounts linked to it. Court records recently released in the federal case against President Donald Trump’s former personal attorney Michael Cohen revealed that another type of cell site simulator, the “triggerfish,” had been used in that investigation.
The most in-depth explanation of what cell site simulators are, and how law enforcement use them as surveillance tools, can be found at the Electronic Frontier Foundation.
In recent years there has been progress, both in court and in state legislatures, to mandate more oversight for StingRay searches, but law enforcement continue to use StingRay devices to identify and track people without a warrant in many states. And because the devices allow law enforcement to track cell phones without going through third-party services like phone companies, they can circumvent checks on their activities to prevent them from abusing the surveillance technology.
Even in the case of a criminal investigation involving a clear warrant to use these devices, the innocents’ privacy rights could still be violated. Cell site simulators don’t just affect a suspect’s cell phone: they can connect to the phones of anyone in their radius - including through the walls of private residences - enabling them to collect identification from other phones in the vicinity as well.
“[This technology] doesn’t just affect particular suspects’ phones but affects essentially large numbers of bystanders who just happen to be nearby,” ACLU attorney Nate Wessler told MuckRock. “Because cell site simulators connect to every phone on the network that’s being impersonated and forces all those phones to reply back, the technology is essentially engaging in a dragnet search and identifying lots of people for whom there is no suspicion whatsoever, let alone probable cause.”
Wessler, who works on the ACLU’s Speech, Privacy and Technology Project, added that although there are now guidelines for the use and acquisition of StingRay devices at the federal level, there has historically been little to no judicial oversight at the state and local levels.
What’s the big deal?
As long as law enforcement is only using the devices to track down criminals, and as long as they’re required to get a warrant, why should the average law-abiding citizen be concerned?
“For a long time police departments and law enforcement agencies across the country were deliberately hiding the fact of their use of this technology from judges as well as from defense attorneys and others,” Wessler said. “Even when they were applying for some kind of judicial authorization, typically the application would not make clear that police intended to use a cell site simulator - the investigative notes wouldn’t reveal if they had used [one] - so judges or defense attorneys later would have a very hard time figuring it out. And that means that judges were completely deprived of the power to limit or prohibit use of this technology.”
Cell site simulators themselves were largely unheard of before the fascinating 2013 court case U.S. v. Rigmaiden, which led to revelations about their use in tracking suspects. Tax scammer Daniel Rigmaiden, representing himself in court, uncovered the secretive StingRay project, prompting investigations by privacy rights organizations and journalists to uncover more information about their availability and use at law enforcement agencies across the country.
Wessler said that while there’s no evidence of cell site simulators being used to indiscriminately collect personal data or listen to personal phone calls, the technology’s capability to do so - coupled with the lack of oversight on law enforcement’s use of this technology - is more than a little concerning.
“There certainly are types or versions of this technology that have the capability to actually listen into cell phone calls or intercept the contents of text messages or data connections,” he said. “There may also be ways in which versions of the technology can be programmed to transmit stuff stored in the memory of those phones, to access data. I think much less is known about those capabilities other than that it is technologically possible to exploit vulnerabilities in how phones operate to remotely make them send data.”
After the 2017 Women’s Marches, MuckRock asked nearly 200 police departments around the country about their use of cell site simulators to monitor or track demonstrators. Only 35 responded substantively, while the rest either ignored the requests or cited indiscriminate exemption policies.
Despite a lack of concrete evidence that StingRay devices have collected data on people who aren’t under criminal investigation, Wessler said that considering the device’s secretive history, more transparency is the best way to ensure that doesn’t happen.
“It is totally inconsistent with our system of democratic and judicial oversight for police to be operating in secret using increasingly sophisticated and powerful surveillance tools,” he said. “It’s important for local and state legislatures so they can set the rules, and then it’s also important for individual people so they can see if they’ve been subject to surveillance and, if so, can decide if they feel their constitutional rights have been violated and they can ask a judge to decide whether in fact that happened.”
Why the Millions March case matters
Dann told MuckRock that after the NYPD was ordered to issue a non-Glomar response to Millions March NYC’s request in January, they claimed to have no responsive documents because “they do not engage in targeted or blanket interference with protestor’s phones.” Still, the Millions March case sets a precedent for contesting vague non-responses to public records requests not only around law enforcement surveillance of protestors, but to requests in general.
“It also implicates the NYPD’s use of Glomar in any other contexts, since future courts can cite this decision finding that Glomar is limited, that the NYPD doesn’t have unfettered discretion to assert it whenever it wants, and that vague claims that information may have something to do with anti-terrorist police work are insufficient to merit Glomar’s protections,” Dann said.
The Millions March decision sets a precedent for greater transparency around cell phone surveillance and could prevent law enforcement from using this indiscriminate excuse to keep their surveillance activity under wraps.
“For years there was extraordinary secrecy over the existence, let alone the use, of this technology such that judges and defense attorneys just didn’t even know it existed. And that secrecy I think was really not in the service of legitimate law enforcement purposes, but it was in the service of impunity,” Wessler said. “It’s a whole lot easier to use powerful, surreptitious surveillance equipment if nobody knows about it and therefore can’t ask questions or challenge it.”
Who’s using StingRay devices?
MuckRock, using public records requests, has been tracking law enforcement agencies that use these devices. The data for that project is located here and includes information on which agencies have responded to our requests and how.
-
Awaiting Acknowledgement: Blue
-
Awaiting Response: Purple
-
Rejected: Large Red
-
Completed: Green
-
No Responsive Documents: Small Red
-
Payment Required: Yellow
The ACLU has been documenting knowledge of cell site simulator use as well, and their data can be perused here.
Projects like these reveal just how ubiquitous cell phone tracking devices have become. From Las Vegas, Nevada to Indianapolis, Indiana to Rochester, New York, it’s clear that StingRay devices have become an increasingly common part of American law enforcement’s surveillance toolkit.
Sometimes, local law enforcement will gain access to this technology through county, state or federal agencies. The District Attorney’s office in Alameda County, California, for instance, has an agreement with at least the Oakland and Fremont police departments to share their tracking devices. And at the national level, the Department of Homeland Security has helped local and state law enforcement purchase StingRay technology through various federal grants.
Representing a victory for transparency advocates looking to challenge the Glomar response, the Millions March case could result in additional record releases.
You can help. Let us know where to shed light on the issue and signing up for updates below.
Image by Phil Roeder via Flickr and is licensed under CC BY 2.0