A series of recently released legal guidelines on Open Source Intelligence explain how and when intelligence agencies can exploit social media and other online resources. One of the documents, previously classified SECRET//NOFORN, hints at the online recruitment of people as sources of information. Collectively, the guidelines spell out the restrictions intelligence agencies work with when dealing with OSINT, revealing how users and developers can deter intelligence agencies from some of the most casual, and pervasive, forms of surveillance.

The first document, a previously SECRET set of guidelines, discuss the collection, exploitation, retention. and dissemination of social media information, including crowdsourced information, as well as touching on participation in U.S. organizations for intelligence purposes.

As the guide explains, it includes the concept of crowdsourcing in its discussion of social media, including the former within the definition of the latter. The guidelines identify Facebook, Twitter, Flickr and YouTube as obvious forms of social media, as well as “WikiMaps” and OpenStreetMaps as examples of crowdsourced information. The inclusion of crowdsourced maps makes sense in light of the fact that the guidelines were produced by the National Geospatial Intelligence Agency, though the guidelines also mention using Wikipedia as a source of crowdsourced information.
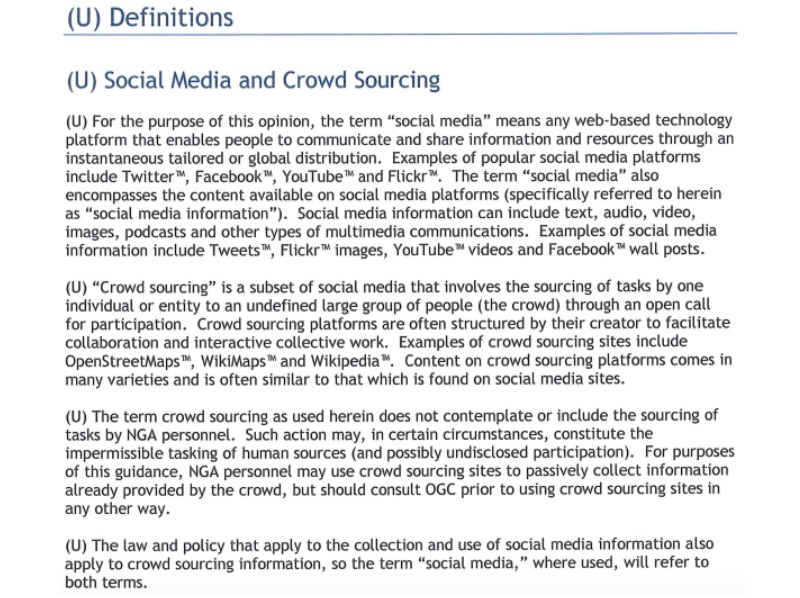
The guidelines also note that they do not discuss or address NGA personnel tasking crowdsourcing sites, since this might “constitute the impermissible tasking of human sources (and possibly undisclosed participation).” Instead, the guidance limits itself “to passively collect[ing] information already provided by the crowd.” As the guidelines soon note, the cited restriction on using human sources is specific to the NGA.

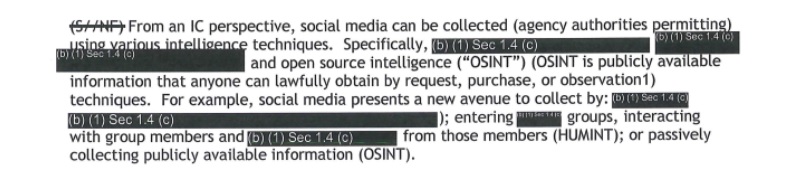
One section, which remains partially classified, discusses secret collection techniques, including “entering [redacted] groups” and “interacting with group members and [redacted] from those members” in what the guidelines identify as a form of HUMINT, or Human Intelligence. While NGA is largely prohibited from recruiting human sources online, that restriction doesn’t apply to the Intelligence Community as a whole.
What does apply to the IC as a whole is participating in U.S. based organizations - or more accurately, the undisclosed participation in U.S. based organizations. As the NGA guidelines note, social media platforms and groups within them may be considered U.S. organizations if they’re primarily based in the U.S. or are a large number of their members are U.S. persons.

As both the Executive Order and the Office of the Director of National Intelligence’s guidelines make clear, the issue of disclosure is hardly one of transparency. The only disclosure of participation that needs to be made is to “appropriate officials of the organization.”

Who are the “appropriate officials?” Almost certainly not the people who are being used. According to one Homeland Security office, examples include “an executive officer of the organization or an official in charge of membership, attendance, or the records of the organization.” In some instances, the DHS’ Office of Intelligence and Analysis would be disclosing its participation to itself. The DHS guidance asserts that this would be fine so long, as that person was “the most senior official” in the group.

The DHS guidance also note that their office is prohibited from influencing those groups, unless it’s part of an FBI investigation or the group isn’t made up primarily of U.S. persons and is “believed to be acting on behalf of a foreign power.”

However, intelligence personnel are free to collect the information without restriction if it doesn’t require registration and if they maintain a “fly on the wall” status. Similarly, attendance at meetings isn’t a problem if the meetings can be readily accessed by the public at large.

Notably, the NGA’s guidelines specify that collection authorizations are impacted by Licensing Agreements and Terms of Service, which “may provide guidance about … how information may be used and disseminated.” NGA personnel are specifically advised to consult the Privacy Policy, to check who owns the copyright of information and content on the site, and to prefer Terms of Use that “expressly permit redistribution of the data or ruse for non-commercial purposes.”

Since “violating the Terms of Use carries legal implications,” NGA personnel are instructed to consult the Office of General Counsel whenever the circumstances and permissibility aren’t clear in regards to the Terms of Service.

Perhaps surprisingly, copyright can be a stumbling block to government reuse. The guidance notes that “administrative uses of copyrighted information likely require a license or permission.” While “national security uses, such as matching a photograph of a building to classified imagery for a classified intelligence analysis, may qualify as fair use” NGA personnel are still instructed to “get specific advice on whether copyright information may be used without permission, and guidance on when photographs may be used as part of a national security analysis under a fair use theory.”

While most of the restrictions discussed in the Executive Order, DHS guidance, ODNI guidance, and NGA guidance can be bypassed with authorizations ranging from warrants to simple legal consults, the need to jump through these legal loopholes can still act as a deterrent to some of the most pervasive and casual forms of surveillance. Users can trigger these restrictions through careful control of their privacy settings, monitoring how they interact with groups, and doing everything they can to maintain the copyright of materials they posted online. Developers can help by giving users as much control as possible and by ensuring that the Terms of Service allow creators to maintain the copyright of their posts. Developers can also tailor the Terms of Service to prohibit, or at least restrict, using their services to collect information without a warrant or other legal authorization - even if the information would otherwise be publicly available.
You can read the NGA guidance below, and additional guidance from other agencies on the request pages.
Like Emma Best’s work? Support her on Patreon.
Image via Defense.gov